
With an escalation in hackings over the past decade, breaches in our private data are of ubiquitous meaning now, more than ever and for this, encryption is key. Encryption is the process of taking readable data and alters it so that it appears random, it is the process of converting plaintext to cipher text and only authorized parties can understand the information.
The incredible growth of the Internet and web 20 has excited businesses and consumers with its promise of changing the way we live and work. It is extremely easy to buy and sell goods all over the world while sitting in front of a laptop. However, security is a major concern on the Internet, especially when you are using it to send sensitive information between parties.
Encryption is the key building block of internet trust; it protect user data from being exposed, protect sensitive documents and make sure that your communication is not vulnerable with the use of a key. Strong encryption is fundamental to our security, confidentiality, and privacy of data being stored or transferred. It is key to the functioning of many key elements in our society such as secure messaging, e-commence and web browsing.
Besides social media accounts and different applications, personal identifying information such as credit-card information, Social Security numbers, private correspondences, personal details, sensitive company information and bank-account information are considered sensitive. Personally identifiable information (PII) is any data that can be used to identify a specific individual. Sensitive Personal Identifying Information (PII) defined as information that if lost, compromised, or disclosed could result in substantial harm, embarrassment, inconvenience, or unfairness to an individual.
In general terms, it is any information that can be used by criminals to conduct identity theft, blackmail, stalking, or other crimes against an individual. Most popular apps make use of encryption to retain user safety, whether that is for storing data, or for data in transit.
Three reasons why encryption matters;
- Internet privacy concerns are real
Encryption helps protect your online privacy by turning personal information into “for your eyes only” messages intended only for the parties that need them — and no one else.
- Hacking is big business
Cybercrime is a global business, often run by multinational outfits. Many of the large-scale data breaches that you may have heard about in the new demonstrate that cybercriminals are often out to steal personal information for financial gain.
- Regulations demand it
The Health Insurance Portability and Accountability Act (HIPAA) requires healthcare providers to implement security features that help protect patients’ sensitive health information online.
Institutions of higher learning must take similar steps under the Family Education Rights and Privacy Act (FERPA) to protect student records. Encryption helps businesses stay compliant with regulatory requirements and standards. It also helps protect the valuable data of their customers.
Types of encryptions;
- Symmetric encryption – uses a single key to encrypt as well as decrypt data. The key needs to be shared with all authorized people.
- Asymmetric encryption – Also called public key cryptography, asymmetric encryption uses two separate keys, one public (shared with everyone) and one private (known only to the key’s generator). The public key is used to encrypt the data and the private key helps to decrypt it.
The LGBTQ community already faces a lot of discrimination in the society and lack of encryption can increase the disadvantages. For them to have privacy while coming out and connecting with each other, to find support systems online and better access to health care and protection against discrimination of employment and housing from some governments. Journalist relies on encryption to carry out their tasks, protecting the integrity of information and holding government and institutions accountable, they need encryption in order to publish risky stories. Children are highly vulnerable as they are glowing up online doing their school work and thus encrypted services means that parents can rest easy knowing that their children‘s private communications with friends won’t be intercepted.
The internet society is actively working to improve the implementation and adoption of strong encryption across the internet ecosystem and to safe guard encryption from being undermined, either by government proposals for law enforcement access or attempts by the private sector to enable greater data collection and monetization.
Encryption requires the use of an encryption key: a set of mathematical values that both the sender and the recipient of an encrypted message know. Below is an example of Caesar Cipher, a type of cryptography in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet.
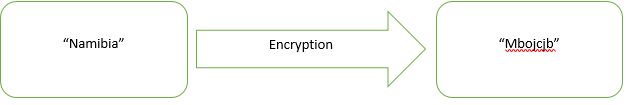
This is a plaintext this is a cipher text
Caesarshift is one of the simplest and most widely known encryption techniques.
There are other methods of encryptions such as:
- Advanced Encryption Standard (AES) – The AES has three fixed 128-bit block ciphers with cryptographic key sizes of 128, 192 and 256 bits. Key size is unlimited, whereas the block size maximum is 256 bits.
- Rivest-Shamir-Adleman (RSA) – this system, a user secretly chooses a pair of prime numbers p and q and find the product n. it generates a pair of keys. Since it generates these keys using a one-way function, it is impossible to generate a private key after knowing the public key.
- Triple Data Encryption Standard (TripleDES) – is a type of computerized cryptography where block cipher algorithms are applied three times to each data block. Each block contains 64 bits of data.
- Twofish – It’s a symmetric key block cipher with a block size of 128 bits, with keys up to 256 bits, it uses pre-computed, key-dependent S-boxes. An S-box (substitution-box) is a basic component of any symmetric key algorithm that performs substitution.
In Namibia currently, there is a greater need to create awareness and provide information on encryption, its benefits, why it is needed and how it works. No matter the method or the reason, there is no encryption backdoor that doesn’t weaken security for all the service’s users, therefore some governments call to create ways for them to access the content encrypted by the companies’ systems (known as “encryption backdoors”) should not be accepted.
By Loide Uuzigo
For Encryption for Everyone Initiative




There is definately a great deal to find out about this subject. I love all the points you have made.
Spot on with this write-up, I actually believe that this website needs much more attention. I’ll probably be back again to see more, thanks for the information!
Good web site you have got here.. It’s difficult to find high quality writing like yours nowadays. I really appreciate individuals like you! Take care!!
Thanks for any other informative website. Where else may I get that type of info written in such a perfect manner? I have a venture that I am just now working on, and I have been at the look out for such info.